What is FakeAV?
What is FakeAV?
FakeAV or Fake AntiVirus, also known as Rogue AntiVirus, Rogues, or ScareWare, is a class of malware that displays false alert messages to the victim concerning threats that do not really exist. These alerts will prompt users to visit a website where they will be asked to pay for these non-existent threats to be cleaned up. The FakeAV will continue to send these annoying and intrusive alerts until a payment is made. This paper provides insight into where FakeAV comes from, what happens when a system is infected with FakeAV, and how users can protect themselves from FakeAV.
During the last year, the number of FakeAV executables has grown enormously. This huge rise in popularity among malware writers is primarily due to the direct revenue source that FakeAV provides. Compared to other classes of malware such as bots, backdoor Trojans, downloaders and password stealers, FakeAV draws the victim into handing money over directly to the malware author.
Typical signs of infection
Popup warnings: Many FakeAV families will display popup messages in the taskbar:
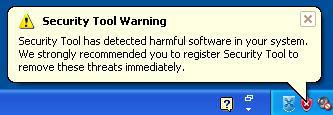
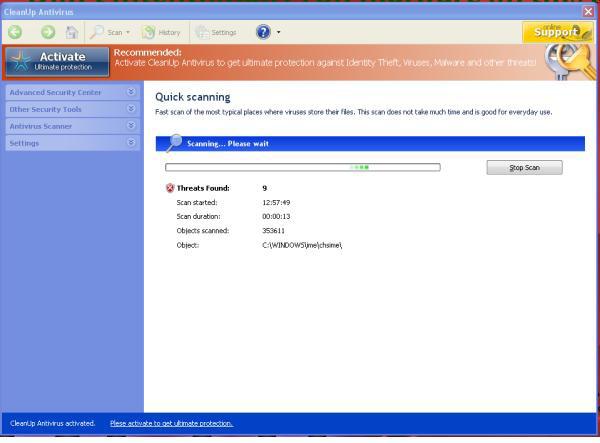
Fake scanning: The FakeAV will typically pretend to scan the computer and find non-existent threats, sometimes creating files full of junk that will then be detected
How do people get infected with FakeAV?
Although there are many different ways that a specific FakeAV may get onto a system, the majority of distribution avenues rely on social engineering. Ultimately, the user is tricked into running the FakeAV installer executable in a way similar to many other types of Trojans. FakeAV authors have used a huge range of different social engineering tricks and are continuing to come up with new ones all the time.
Main sources of infection
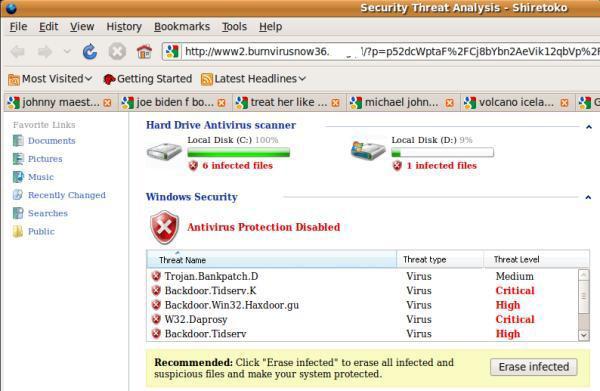
Search engine optimization poisoning: A very common source of FakeAV infection is following results received from popular search engines while searching for topical terms. FakeAV authors ensure that links leading to FakeAV download sites will feature prominently in search results by using blackhat SEO techniques. These poisoned results will redirect users to a FakeAV-controlled website that displays a fake scanning page, informing them that their computer is infected and they must download a program to clean it up. Alternatively, a fake movie download page may be displayed, where users are prompted to download a codec in order to view the movie. This codec is in fact a FakeAV installer.
Email spam campaigns: FakeAV is often sent directly to the victim as an attachment or as a link in a spam message. The message is predominantly sent through email, but other forms of spam have also been observed to deliver FakeAV, such as instant messaging applications. The spam message itself usually uses social engineering techniques to trick users into running the attached file or clicking on the link. Specific campaigns vary and include password reset, failed delivery message and “You have received an ecard” scams.
Account suspension scams:
Victims receive an email message suggesting access to a specific account has
been terminated and they need to run the attached file to fix the issue
Password rest scams: Victim’s receive a message supposedly from a popular website, informing them that their password has been reset and a new one is in the attached file.
Compromised websites and exploit payloads: Users can sometimes be sent to FakeAV websites by browsing legitimate websites that have been compromised, where malicious code has been injected into the page. This can be achieved by penetrating the target website’s hosting server and appending (typically) JavaScript to HTML pages hosted there. This redirect code can be used to send the browser to any type of malware hosting page including exploit kits and FakeAV. This JavaScript code is almost always heavily obfuscated, also hackers have been known to compromise legitimate web-based advertising feeds to ensure that malicious code is loaded instead. This may take the form of an exploit that downloads and executes a FakeAV binary as the payload or a simple iframe that redirects the browser to a FakeAV web page.
FakeAV downloads by other malware: FakeAV can be downloaded onto a machine by other types of malware. Several malware families are known to install FakeAV onto an infected machine, most notably TDSS, Virtumundo and Waled. The infamous Conficker worm was also observed to install FakeAV onto infected computers. In this way, a hacker that has infected a computer with TDSS or Virtumundo can extract more money from victims by forcing them to pay for FakeAV.
What happens when the FakeAV installs
FakeAV’s typical behavior is to copy the installer to another location on the system and create a registry entry that will run the executable on system startup.The installer is often copied into the user’s profile area (e.g., C:\Documents and Settings\<user>\Local Settings\Application Data), or into the temporary files area (e.g., c:\windows\temp) with a randomly generated file name. This makes the FakeAV UAC-compliant on Windows machines that have UAC enabled, thus avoiding a UAC warning popping up during installation. However, some families still do not care about UAC and still create their files in the Program Files or Windows folders.
A run key entry is then created in the registry that will run the file when the system starts up. Typically, this will be added to one of the following:
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run
Once the fake threats have been discovered, users are told they must register or activate the product in order to clean up the threats. Users are taken to a registration website (either through a browser or through the FakeAV application), where they are asked to enter their credit card number and other registration details. These pages are also very convincing, occasionally featuring illegal use of logos and trademarks from industry-recognized organizations.
Certain FakeAV families cause further distress to the victim by interfering with normal system activity. Commonly, this includes disabling the Task Manager and use of the Registry Editor, prohibiting certain processes from running and even redirecting web requests. This behavior further convinces the user that there is a problem on the system and increases the likelihood of a purchase being made. This activity can take the form of:
- Process termination: Certain programs are prohibited from running
- Webpage redirection: Some FakeAV apps will redirect web request for legitimate web sites to an error message
- Installation of more Malware: download other types of malware upon installation, such as banking Trojans, rootkits and spam bots

